Solution for the 0x204 error when connecting to Windows Virtual Desktop (WVD)
Solution for the 0x204 error code when connecting to Windows Virtual Desktop (WVD)
Introduction
While migrating a customer to Windows Virtual Desktop, some users were unable to connect to their WVD desktop/app.
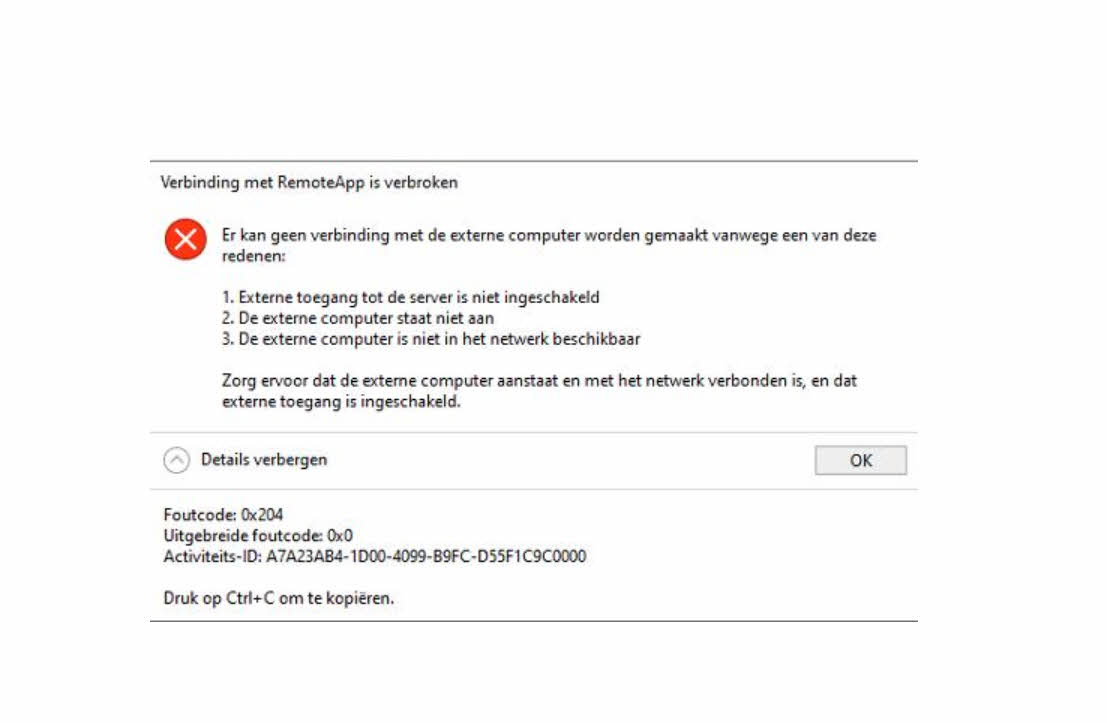
All these users got an error while connecting with this error message: Error code: 0x204
You can find a screenshot & exact error message at the end of the article.
After some research and Wireshark tracing, we found out that the computers were unable to connect to the Windows Virtual Desktop service using a correct Cipher.
How to check?
Open up an elevated PowerShell window with Administrative privileges.
Run the following command to check if you have the default Cipher enabled:
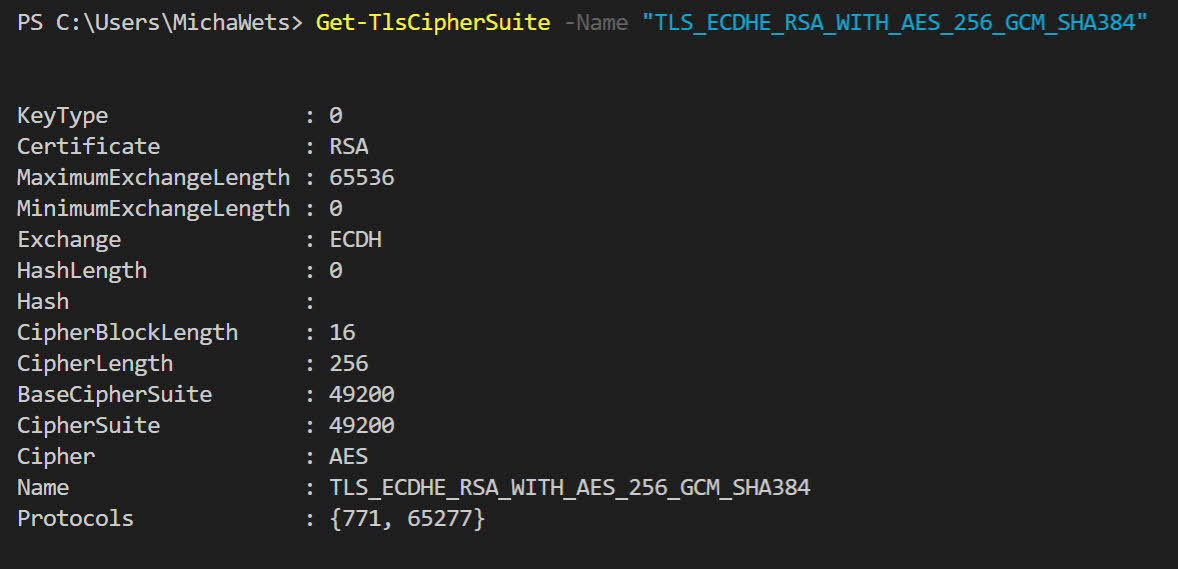
Get-TlsCipherSuite -Name "TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384"
If you get no result back, the Cipher is not enabled, which could cause the issue
Next, you can check if it set by a Policy:
$regValue = Get-ItemProperty -Path "HKLM:\SOFTWARE\Policies\Microsoft\Cryptography\Configuration\SSL\00010002" -Name "Functions" -ErrorAction SilentlyContinue
if ($null -ne $regValue) {
Write-Warning "You have a policy enabled to specify allowed Ciphers on your machine! You should update this to the latest Ciphers!"
}
When you get a Warning back, you should check your Domain Policies (GPOs) or Local Policy settings to verify if the correct Cipher list is enabled.
Policy Solution
You can find the Policy here:
Computer Configuration > Administrative Templates > Network > SSL Configuration Settings > SSL Cipher Suite Order
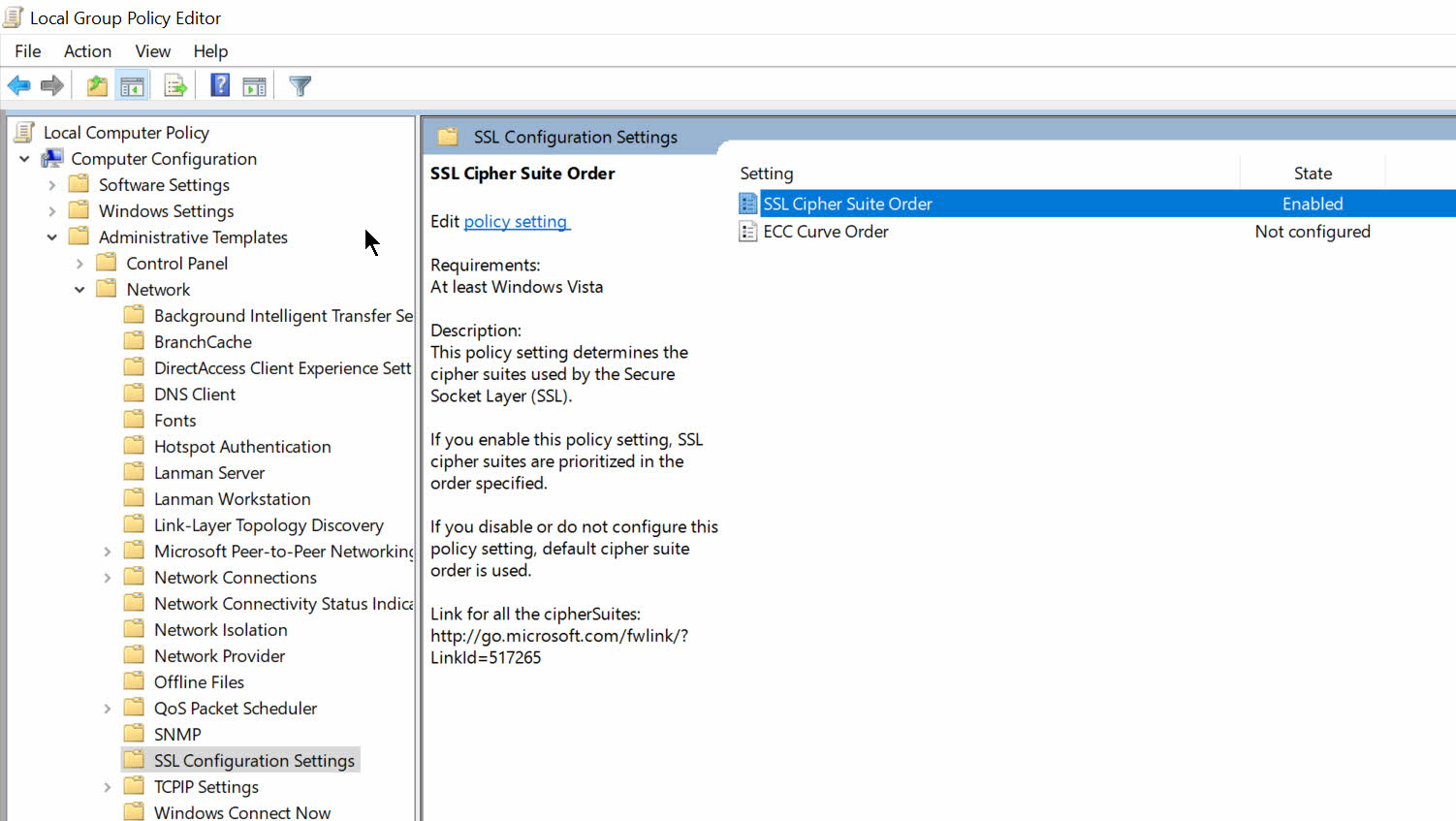
This is the default list on a Windows 10 machine:
TLS_AES_256_GCM_SHA384,TLS_AES_128_GCM_SHA256,TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_DHE_RSA_WITH_AES_256_GCM_SHA384,TLS_DHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA,TLS_RSA_WITH_AES_256_GCM_SHA384,TLS_RSA_WITH_AES_128_GCM_SHA256,TLS_RSA_WITH_AES_256_CBC_SHA256,TLS_RSA_WITH_AES_128_CBC_SHA256,TLS_RSA_WITH_AES_256_CBC_SHA,TLS_RSA_WITH_AES_128_CBC_SHA,TLS_RSA_WITH_3DES_EDE_CBC_SHA,TLS_RSA_WITH_NULL_SHA256,TLS_RSA_WITH_NULL_SHA,TLS_PSK_WITH_AES_256_GCM_SHA384,TLS_PSK_WITH_AES_128_GCM_SHA256,TLS_PSK_WITH_AES_256_CBC_SHA384,TLS_PSK_WITH_AES_128_CBC_SHA256,TLS_PSK_WITH_NULL_SHA384,TLS_PSK_WITH_NULL_SHA256
Don’t forget to run a gpupdate after setting the Domain or Local policy!
gpupdate /force /target:computer
Manual Solution
If that does not resolve the issue, you can manually try to enable the Cipher:
Enable-TlsCipherSuite -Name "TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384"
Here is a script which will enable all current Ciphers default on a Windows 10 2004 build:
$defaultCyphers = @("TLS_AES_256_GCM_SHA384","TLS_AES_128_GCM_SHA256","TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384","TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256","TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384","TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256","TLS_DHE_RSA_WITH_AES_256_GCM_SHA384","TLS_DHE_RSA_WITH_AES_128_GCM_SHA256","TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384","TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256","TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384","TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256","TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA","TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA","TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA","TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA","TLS_RSA_WITH_AES_256_GCM_SHA384","TLS_RSA_WITH_AES_128_GCM_SHA256","TLS_RSA_WITH_AES_256_CBC_SHA256","TLS_RSA_WITH_AES_128_CBC_SHA256","TLS_RSA_WITH_AES_256_CBC_SHA","TLS_RSA_WITH_AES_128_CBC_SHA","TLS_RSA_WITH_3DES_EDE_CBC_SHA","TLS_RSA_WITH_NULL_SHA256","TLS_RSA_WITH_NULL_SHA","TLS_PSK_WITH_AES_256_GCM_SHA384","TLS_PSK_WITH_AES_128_GCM_SHA256","TLS_PSK_WITH_AES_256_CBC_SHA384","TLS_PSK_WITH_AES_128_CBC_SHA256","TLS_PSK_WITH_NULL_SHA384","TLS_PSK_WITH_NULL_SHA256")
foreach ($cypher in $defaultCyphers) {
Enable-TlsCipherSuite -Name $cypher
}
Result
After fixing the Policy or enabling the Ciphers by script, you should get this result after running and you should be able to connect to your Windows Virtual Desktop Desktop/App
Get-TlsCipherSuite -Name "TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384"
Screenshot & error message
[Window Title]
RemoteApp Disconnected
[Content]
Remote Desktop can't connect to the remote computer for one of these reasons:
1) Remote access to the server is not enabled
2) The remote computer is turned off
3) The remote computer is not available on the network
Make sure the remote computer is turned on and connected to the network, and that remote access is enabled.
[^] Hide details [OK]
[Expanded Information]
Error code: 0x204
Extended error code: 0x0
Activity ID: D5094B06-0A73-4BC4-BD91-80897A380000
Comments
We hope this helps! Please leave a comment below if you have questions or remarks.